Malware Analysis: Android Malware Disguised as GB WhatsApp
- May 13, 2025
- 3 min read
Updated: Dec 9, 2025

Today I’m diving into an Android APK, most likely from the Joker malware family.
The sample hides as the WhatsApp mod “GB WhatsApp” and masquerades as a harmless chat‐upgrade so users sideload it without a second thought.
Sample details
SHA‑256 : a59ceb42de98795df657e636aec45ded7208f689fffc1d228dce941d95750423 Size : 67.18 MB1. Opening the APK in JADX
I load the file in jadx and instantly spot the package name:
com.gbapp.gbThat’s the bundle ID used by the real GB WhatsApp mod.

2. First red flags – intent queries
I immediately saw intent queries for Meta apps (Facebook, Oculus, Messenger). In a legit app that isn’t alarming, but in malware, it usually means fingerprinting:

A second tell‑tale tag confirms the idea:
<intent> <action android:name="whatsapp.payments.intent.action.STEP_UP"/> </intent>That looks like a probe to check whether WhatsApp’s internal payment setup is available on the device.
3. Permission review
The <uses‑permission> section is huge, so I’m cherry‑picking the shadiest groups.
Data‑theft & surveillance
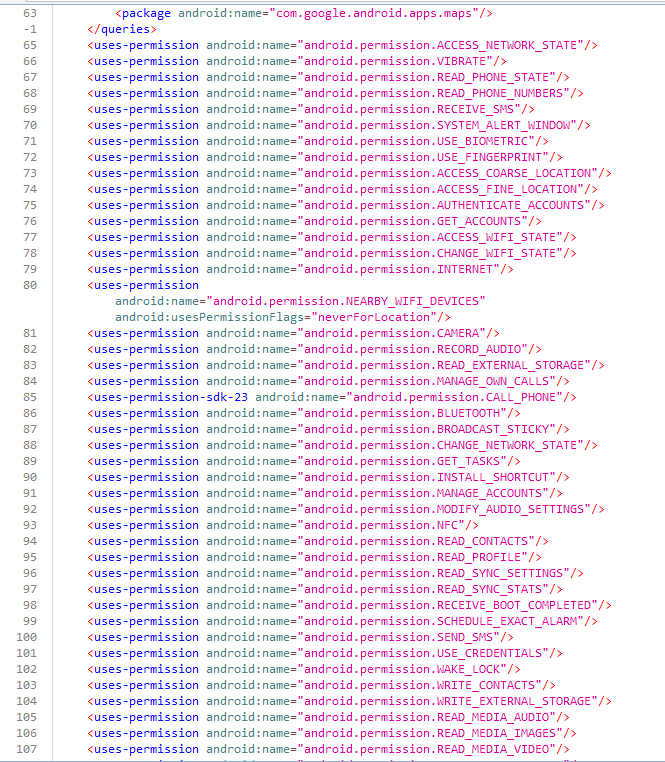
<uses-permission android:name="android.permission.READ_CONTACTS"/> <uses-permission android:name="android.permission.READ_PROFILE"/> <uses-permission android:name="android.permission.WRITE_CONTACTS"/>Steal, read, and edit the address book.
<uses-permission android:name="android.permission.RECEIVE_SMS"/> <uses-permission android:name="android.permission.SEND_SMS"/>Full SMS control → OTP interception, spyware.
<uses-permission-sdk-23 android:name="android.permission.ANSWER_PHONE_CALLS"/> <uses-permission-sdk-23 android:name="android.permission.READ_CALL_LOG"/> <uses-permission-sdk-23 android:name="android.permission.CALL_PHONE"/>Voice call hijacking and logging.
<uses-permission android:name="android.permission.CAMERA"/> <uses-permission android:name="android.permission.RECORD_AUDIO"/> <uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>Camera, mic, GPS – classic spy‑app trio.
Persistence
android:name="android.permission.RECEIVE_BOOT_COMPLETED"/> <uses-permission android:name="android.permission.WAKE_LOCK"/> <uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>RECEIVE_BOOT_COMPLETED – autostart after reboot.
WAKE_LOCK – keep the app alive.
FOREGROUND_SERVICE – long‑running code, usually hidden behind a silent notification.
Advanced abuse

<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>Draw‑over‑apps → phishing overlays.
<uses-permission android:name="android.permission.REQUEST_INSTALL_PACKAGES"/>Download & install additional APKs (second‑stage payloads).
<uses-permission android:name="android.permission.MODIFY_AUDIO_SETTINGS"/>Mute alerts while spying.
<uses-permission android:name="android.permission.SCHEDULE_EXACT_ALARM"/>Stealthy background job scheduling.
Suspicious custom permissions
com.gbapp.gb.permission.* com.whatsapp.sticker.*Hand‑rolled permissions – common in mods that bypass OS checks or mimic legit services.
Ad‑tracking
<uses-permission android:name="com.google.android.gms.permission.AD_ID"/> <uses-permission android:name="com.google.android.providers.gsf.permission.READ_GSERVICES"/>Standard ad‑ID scraping to track users.
4. Embedded banking components (!)
Major discovery:

<activity android:name="org.npci.upi.security.pinactivitycomponent.UserAuthInfoActivity"/> <activity android:name="org.npci.upi.security.pinactivitycomponent.GetCredential"/> <service android:name="org.npci.upi.security.pinactivitycomponent.CLRemoteServiceImpl"/>org.npci.upi.security.* is reserved for legit Indian UPI banking apps. Here it’s bundled stealthily (excludeFromRecents, hidden orientation flags). That screams credential phishing.
5. Massive fake‑payment surface
Searching for “payment” yields dozens of activities under:
com.gbapp.gb.payments.*
phoenix.flowconfigurationservice.activities.*

Fake UPI flows
com.gbapp.gb.payments.ui.IndiaUpiCreateCustomNumberActivity com.gbapp.gb.payments.ui.IndiaUpiPauseMandateActivity com.gbapp.gb.payments.ui.IndiaUpiProvideMoreInfoBottomSheetActivityCustom UPI screens → PIN harvesters.
Brazilian payment fraud
com.gbapp.gb.payments.ui.BrazilPaymentActivity com.gbapp.gb.payments.ui.BrazilFbPayHubActivity com.gbapp.gb.payments.ui.BrazilPaymentCardDetailsActivityTargets Brazil’s WhatsApp Pay.
WebView phishing
com.gbapp.gb.payments.ui.PaymentWebViewActivity com.gbapp.gb.payments.ui.MessageWithLinkWebViewActivityLoads fake portals, injects JS.
PIN / fingerprint abuse
IndiaUpiFcsResetPinActivity IndiaUpiFcsConsumerOnboardingActivity IndiaUpiFcsPinHandlerActivityCredential harvesters wrapped as “security” flows.
Alert & CSAT manipulation
com.gbapp.gb.framework.alerts.ui.AlertCardListActivity com.gbapp.gb.payments.care.csat.CsatSurveyBloksActivityFake customer‑support to deflect complaints.
Bottom line: multi‑region payment spoofing, zero legitimate SDKs, heavy obfuscation.
6. strings.xml highlights
Digging into strings.xml, I spot some suspicious entries:
<string name="fkf">E1E1C343CE08185001D4E3F6757541EB</string>Looks like an MD5 / XOR key – no public matches.
Another gem links to YoWhatsApp (another mod infamous for spyware):
<string name="yoDonateSum">Keep YoWA alive!</string>That sparks a quick IOC hunt and exposes a donation system:
<string name="donateMe">Do you find this application useful?\nSupport its development by sending a donation to the developer!</string> <string name="donations__paypal">PayPal</string> <string name="donations__bitcoin">Bitcoin</string> <string name="donations__google_android_market">Google Play Store</string>
Critical IOC
https://yousefalbasha[.]com/files/lastv6.txtThe dev basically hard‑codes his own domain in the malware. The site is now offline, but Wayback Machine still has snapshots:

Turns out he also authored YoWA:

And the exact IOC appears in those archives:

The key part:
"dli": "https://www.yousefalbasha[.]com/wa/yowa/#dw"Likely opened by the app’s WebView to push updated (malicious) builds.
More (now dead) URLs uncovered:
http://theyocraft[.]com/wmapp

fouadmods[.]com – hub of modded APKs

Wayback shows it redirects to:
https://www.fmmods[.]com/
Which lists countless “tweaked” versions of popular apps – classic malware distribution:

7. Credits section
At the end of AndroidManifest.xml the author leaves a “thank you” roll – probably copied straight from the original mod:

Summary
GB WhatsApp clone bundled with malware.
Grabs contacts, SMS, calls, camera, mic, GPS.
Auto‑starts, keeps awake, installs second stages.
Ships counterfeit UPI / FB Pay / Pix payment screens targeting India & Brazil.
Hard‑coded IOCs tie back to the YoWA developer domain.
Distributed via shady mod portals now mostly offline.
That wraps up my teardown. Any updates or extra findings are welcome, feel free to ping me.




